Cyber Incident Response Drill
March 31, 2021
2 min read
5What is Cyber Incident Response Drill?
“A plan not tested, is not a plan at all”
Cyber Security is a sub-set of Information Security.
But since most information is created, stored and shared through “cyber” means, the terms are often used interchangeably.
Information Security performance in Australia:
The Office of the Australian Information Commissioner (OAIC) publishes annual reports for reported cyber incidents involving personal information.
The following graphs show the OAIC statistics from 1st April 2018 to 31st March 2019:
Notifiable Data Breaches Statistics
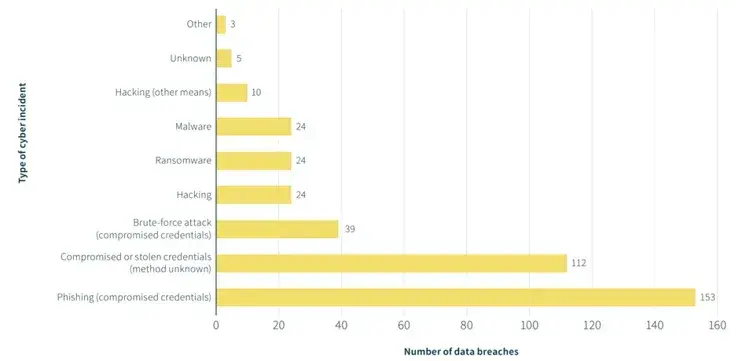
Human Error Causes
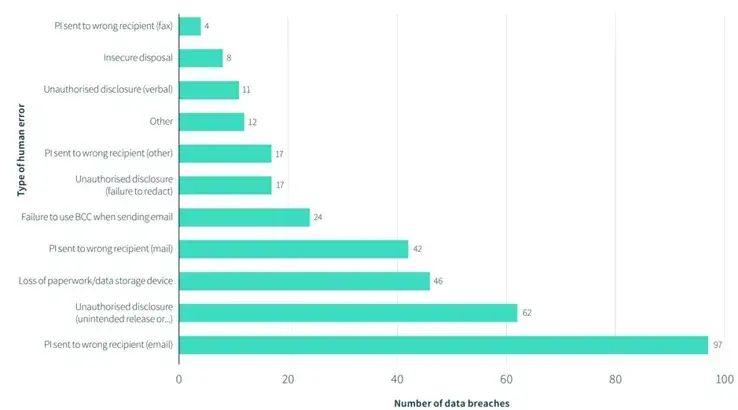
Top Reporting Sectors
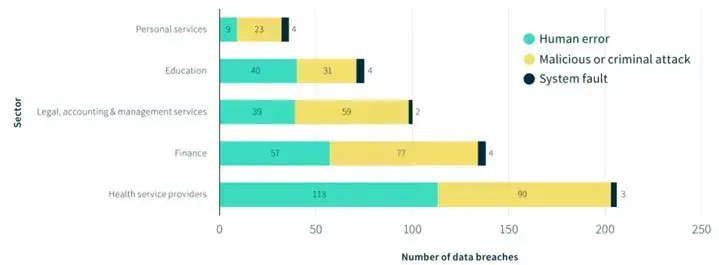
Size of Breaches
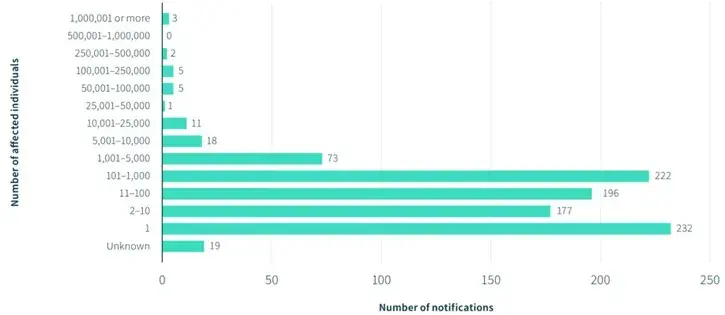
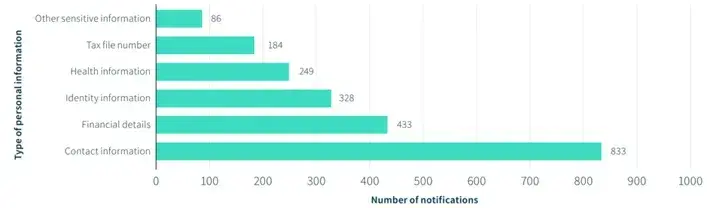
Types of personal Information
The average cost of a cyber incident in Australia is $276,000, according to ReportCyber (formerly ACORN).
Companies of all shapes and sizes are vulnerable to cyber-attacks,Performing the drills helps you to prepare.
Benefits of conducting Cyber drill:
- They test both technical and governance aspects
- They provide performance benchmarks
- They provide valuable insights
- Unique chance for executives to assess their staff’s preparedness as well as their own
- Quality Assurance for third parties.
The objectives of a Cyber drill:
- To test the effectiveness of the CIRP/IR
- To assess the awareness and preparedness of staff
Here at Compliance Council, our team of expert InfoSec Consultants can help you mitigate the risks arising from an attack.
We conduct the drill in two phases:
Phase 1. Preparation
Phase 2. The Drill
The findings are then recorded and documented, decisions are taken on corrective actions and remediations, which helps to establish the benchmark for the future.
Contact Us to find out how we can help you, schedule a complimentary consultation with our Principal Consultant today.
Glossary: Key terms
- Cyber attack: An assault launched by an assailant with the objective of causing damage or gaining a benefit.
- Hacker: Neutral Term. Cyber Criminals are called “Black Hats”. Ethical hackers are called “White Hats”.
- Blue team: The team responsible for the cyber defence of an organisation.
- Red team: The team responsible for simulating an attack to assess current cyber security posture.
- Gold Team: The executive team of an organisation. Responsible for cyber governance and incident decision making.
- Cyber Incident: A cyber attack that was successful in by-passing security controls.
- Information Security controls: Measures taken to mitigate risks facing information assets.
Sign up for our newsletter
Stay Ahead: Subscribe for the Latest Compliance Insights and Updates.
We care about the protection of your data. Read ourPrivacy Policy.


